Updated April 17, 2013: In light of recent events, I’ve decided to remove the ricin recipe plaintext from this post. The FBI, however, continues to display the encrypted ricin recipe on their website.
Cryptographer Klaus Schmeh recently posted about a cryptogram that appears in an FBI article about how their Cryptanalysis and Racketeering Records Unit (CRRU) breaks codes and ciphers to solve crimes.
The FBI article says the cryptogram contains “enciphered instructions for making ricin poison found in the notebook of a lone bomber in Virginia.” I couldn’t find any decryptions of the cipher text, so I transcribed it, and fed it into zkdecrypto lite, which very quickly found a rough approximation of the plaintext. A little bit of extra work yielded the full solution, which really does contain a recipe for ricin poison, encrypted using simple homophonic substitution.
At first I was hesitant to post the solution. Is it irresponsible to reveal a dangerous recipe to the public? But I’ve decided to post it for these reasons:
- The FBI already posted the cryptogram in full view of the public.
- The cryptogram is very easy to solve.
- Ricin recipes are already very easy to come by via Google searches.
- The enciphered recipe is very crude, producing only a mash form that is not further purified for dangerous potential. Similar recipes in terrorist “cookbooks” are “deemed incapable of achieving a good product for causing a large number of casualties by any exposure route, mainly because of the low content of toxin of the final extracts” [1]
- Only one death has been attributed to ricin poisoning. Every other ricin-related incident seems to involve dumbasses stockpiling the stuff for its claimed deadly potential.
Here’s the decoded plaintext:
[redacted]
And here is the full analysis of the solution, including the solution key, symbol cycles, and symbol frequencies.
The cryptogram bears some interesting similarities to the Zodiac’s ciphers: It is 354 characters long (to Zodiac’s 340), has 65 distinct symbols (to Zodiac’s 64 in the 408-character cipher), uses homophonic substitution (like Zodiac’s 408), and uses some of the same symbols. The ricin bomber, however, did not do a good job of concealing the letter frequencies of the plaintext. In fact, if you look at the symbol frequencies, the most common symbols correspond directly to the most common letters in English: E, T, A, O, N, etc. This is because the lone bomber did not correctly flatten the frequencies with the proper number of symbol assignments per plain text letter.
The FBI says this cryptogram is just one small part of 24 pages of enciphered messages. It would be interesting to see what else was in the notebook, and to know more about the bomber. I can’t find any news sources that mention the Virginia lone bomber. Does anyone have any ideas?
Dan Johnson recently posted a really curious discovery about the 340-character cipher on his blog. First, number each of the positions of the cipher from 1 to 340. Then, mark each of the positions occupied by a  symbol, the most common symbol, appearing 24 times in the cipher. You’ll get this list of numbers:
symbol, the most common symbol, appearing 24 times in the cipher. You’ll get this list of numbers:
- 20, 40, 64, 65, 72, 81, 105, 128, 133, 140, 142, 159, 162, 172, 201, 211, 237, 238, 255, 276, 282, 290, 291, 340
Then, mark every number that is a prime number. Recall from your math classes that a prime number is a number greater than 1 that can’t be divided by anything other than 1 and itself. Here’s the result of marking the primes in the above list:
- 20, 40, 64, 65, 72, 81, 105, 128, 133, 140, 142, 159, 162, 172, 201, 211, 237, 238, 255, 276, 282, 290, 291, 340
There’s only one prime number in the list. Dan points out that 20% of the numbers between 1 to 340 are primes, so we should expect more of the  symbols to fall upon prime positions simply by chance. Yet only one does. Is this just a coincidence, or is it some reflection of the cipher author’s method?
symbols to fall upon prime positions simply by chance. Yet only one does. Is this just a coincidence, or is it some reflection of the cipher author’s method?
I ran an experiment similar to Dan’s, using a computer program that randomly places symbols and counts how many primes they fall upon. First, it scrambles the 340 cipher into a random order, like shuffling a deck of cards. Then it counts how many  symbols fall upon prime positions. The result is that out of 1,000,000 random shuffles, only 28,877 of them have exactly 0 or 1
symbols fall upon prime positions. The result is that out of 1,000,000 random shuffles, only 28,877 of them have exactly 0 or 1  symbols falling upon prime positions. That’s about 2.9% of all the shuffles.
symbols falling upon prime positions. That’s about 2.9% of all the shuffles.
That result can be interpreted like this: Let’s say you were creating a 340-character cipher, and you need to place 24 copies of a particular symbol. If you didn’t care at all about whether or not they were placed on primes, then you’d have about a 2.9% chance of avoiding all but one prime position.
So, it’s possible that the cipher’s author accidentally produced this oddity simply by placing the symbols. A 2.9% chance isn’t rare enough to rule out pure coincidence, but it’s certainly curious.
However, Dan goes on further to point out that 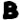 , the 2nd most frequent symbol in the 340 cipher, occurs 12 times and yet also only falls on a single prime position:
, the 2nd most frequent symbol in the 340 cipher, occurs 12 times and yet also only falls on a single prime position:
- 21, 35, 147, 168, 181, 203, 216, 240, 261, 286, 315, 319
The symbols  and
and 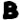 account for 10% of all of the symbols of the 340 cipher, and yet only fall on two primes.
account for 10% of all of the symbols of the 340 cipher, and yet only fall on two primes.
I repeated the “random shuffle” experiment, counting how often  and
and 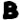 each fall on no more than one prime. The experiment confirmed Dan’s result: Only 0.7% of the shuffles accidentally shared the same quality as the original 340 cipher.
each fall on no more than one prime. The experiment confirmed Dan’s result: Only 0.7% of the shuffles accidentally shared the same quality as the original 340 cipher.
Strange, isn’t it?
What about Zodiac’s previous cipher? Does it show this same strangeness?
The 408 cipher’s most common symbols are 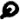 (found 16 times),
(found 16 times),  (found 14 times),
(found 14 times), 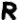 (found 12 times),
(found 12 times), 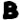 (found 12 times), and
(found 12 times), and 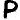 (found 11 times). Three of those symbols fall on non-prime positions all but one time:
(found 11 times). Three of those symbols fall on non-prime positions all but one time:  ,
, 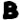 and
and  . Those three symbols account for about 9% of the entire cipher text.
. Those three symbols account for about 9% of the entire cipher text.
Repeating the shuffle test for the 408, I found only 1.8% of the 1,000,000 shuffled 408-character ciphers had this same quality.
Why would the cipher symbols be biased against prime positions? Is there something to this, or are we just chasing noise again?
One way to explore the idea further is to simulate the construction method of the 408 cipher. A computer program could generate a million different real ciphers, using different plain texts and somewhat regular sequences of homophones. Then the program can measure how many of the generated ciphers accidentally have these strange prime properties. Perhaps there is some link between the regular assignment of homophone sequences (or some other aspect of the cipher construction), and the probability that the symbols will fall upon primes.
If the ciphers really are prime-phobic, can this knowledge help us unravel the 340?
German computer scientist and cryptology writer Klaus Schmeh recently published a German-language book about famous unsolved secret messages, including the Zodiac Killer cryptograms.

(The cover depicts what we all probably want to do with Zodiac’s cryptograms.)
Nicht Zu Knacken (which I think roughly translates as Not To Crack) summarizes ten fascinating unsolved mysteries: The Voynich Manuscript
, the Rohonc Codex, James Hampton’s notebook, unbroken Enigma messages
, messages from East Germany that used “double dice” transposition, the mystery of the Somerton Man, the Beale ciphers, Kryptos, Robert Thouless’ Experiment, and of course the ciphers of the Zodiac Killer.
Relying on Google Translate, I tried to digest the chapter on the Zodiac Killer. Klaus first gives a brief summary of the crimes, including a timeline of the letters and codes. He also relates the story of the Hardens’ successful decryption of the 408-character cryptogram. The Hardens were not cryptography experts, but they knew enough about cryptograms to understand the importance of English letter frequencies in attacking substitution ciphers. They also knew the importance of trying out cribs in the cipher text, which successfully revealed other pieces of the plain text. Klaus describes the effect the Hardens’ success had on them. Reportedly, Bettye Harden had trouble dealing with all of the sudden attention and fame, and developed a manic-depressive personality disorder.
Here are some of the other bits of info Klaus mentions:
- Donald Harden was asked to work on the 340-character cryptogram, but refused. However, Bettye “barricaded herself in her room for weeks” to try to solve it, but failed. The CIA and NSA also failed to crack the code.
- The 13-character cryptogram is very difficult to solve, because it is too short for cryptanalysis.
- The Zodiac Killer case went cold in the late 1970s, but then started to heat up again as the Internet became widespread in the late 1990s, and sites such as Tom Voigt’s Zodiackiller.com appeared.
- Robert Graysmith points out in his book “Zodiac
” several cryptography books that were available at the time of the crimes: “The Codebreakers
” by David Kahn, and “Codes and Ciphers
” by John Laffin.
The 340 is still of interest to cryptographers because of its length. The 13 and 32 character cryptograms are simply too short, making definitive solutions very unlikely. But the 340 is long enough to hold out hope for a definitive solution resulting from discovery of an encryption scheme.
Based on symbol frequencies, Klaus observes that the 340 has some homophonic properties (letters in the hidden message might be represented by multiple symbols), suggesting a construction similar to the 408. But he wonders if the same method was used a second time. Since the 408 was solved so quickly, Zodiac could have changed his method, perhaps by adding meaningless letters, or by completely changing his encryption technique.
Homophonic substitution ciphers make decryption difficult, but not impossible, as the Hardens demonstrated. Failing with cribs, one could try to guess common letter pairs. But the 340 does not have much to work with. Another strategy is to look at the homophone order (the sequences of symbols assigned to individual plaintext letters).
While researching his book, Klaus met Austrian Mensa member Jürgen Koller, who was developing his own method of detecting homophone usage in the Zodiac ciphers. His “two-time repetition” approach can be found here. And his Austrian Mensa article about the Zodiac ciphers can be found on page 36 in this “Top IQ” Mensa journal published last year.
Klaus also mentions the Cryptologia paper by John King and Dennis Bahler, An Algorithmic Solution of Sequential Homophonic Ciphers. The method described in the paper is very powerful for attacking cryptograms that are constructed with sequential homophones. You can see the pattern of sequential homophones in this detailed breakdown of the solution to the 408. The 408 is easily cracked by King and Bahler’s method, but no solution is found for the 340 using the same method. I believe the same regularities that make ciphers like the 408 vulnerable to King and Bahler’s technique also make them easily cracked by hillclimbing computer programs such as zkdecrypto.
But the Zodiac killer probably did something unique to the 340 to make it withstand attacks from these various methods. Homemade test ciphers that are 340-characters long and share the same symbol distribution easily fall to these assorted attacks. I don’t think we can keep assuming that a simple substitution attack will work. Something else is probably going on in the encryption scheme in the 340. Or it’s just pointless busywork which continues to hypnotize us nearly a half century after it was created.
What is the “something else” the killer might have applied to the 340-character cryptogram? Klaus mentions Robert Graysmith’s “solution”, but points out the overuse of unusual abbreviations, misspellings, and incomprehensible wording. Those traits are common when you allow anagramming in your approach to the solution (you can see many examples of them here). Klaus also notes Raymond Grant, whose book “The Zodiac Murders – Solved” describes elaborate hidden messages in the Zodiac letters, and is “simply too confusing to be true” and “more of a curiosity than a serious contribution.” Many more ideas have been explored. Hopefully one of them will lead to a breakthrough.
Overall, Klaus Schmeh’s book is very interesting. It goes a bit beyond the usual “Top Unsolved Codes” lists that occasionally appear in the news to tease our thirst for mysteries. Brush up on your German and visit Klaus’ blog in which he unearths more mysteries and tidbits. And watch his appearance on German TV show “Planet Knowledge” during a full hour-long episode about secret codes.
I love that we live in an age where university lectures are frequently made free for all to benefit from. From Nick Pelling’s consistently intriguing site comes news that Kevin Knight, the famed USC researcher whose team cracked an old enciphered German manuscript from the 18th century, and linguistic algorithms researcher Sravana Reddy will be giving a free lecture about the unsolved Voynich Manuscript at Stanford University at 4:15 PM PDT this Wednesday, March 13th.


More information about the lecture can be found here: http://www.stanford.edu/class/ee380/Abstracts/130313.html.
To attend the lecture, go to this site: http://www.stanford.edu/class/ee380/. When the lecture is underway, you can click the “join the live presentation” link, or just wait until the on-demand video is made available there.
Kevin Knight and his colleagues have a lot of very interesting work under their belts, helping to unlock old mysteries with new computational technologies. I look forward to hearing what they know about the Voynich Manuscript, and if their approaches might have any relevance to investigating the Zodiac cryptograms.


Click above to view the entire article as it appeared as the top story in the Leader-Herald, a local newspaper in Gloversville, NY.
The article also appeared online here: Decoding a Killer.
Daryll did not solve Zodiac’s puzzle, and this article explains why. I’m glad people are still trying to solve the cryptograms, but until someone comes up with the real solution, these stories will continue to flourish.
These videos popped up on Youtube recently:
The first video presents this solution to the 340 cipher:
(more…)
I recently saw this post on Twitter:
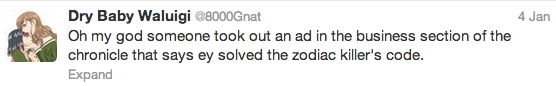
Sounds like a joke at first. But someone really did pay to place this ad in the San Francisco Chronicle newspaper:

It appeared in the December 21, 2012 paper, and appeared three more times on successive Fridays.
The ad provoked my curiosity, so I called Daryll to ask him about his solution. He is a very friendly, older gentleman who lives in upstate New York. He said he has no background in code breaking, apart from working codes as a hobby in the free time resulting from his retirement. He took out the ad in the San Francisco Chronicle because he had submitted his solution to the Vallejo police department and the American Cryptogram Association, and received no responses. His plan was to charge $5 for the solution, but when he realized he wasn’t going to make any money, he decided to mail out copies for free.
I received my copy recently. You can see his worksheets here:
(more…)
In his book Zodiac, Robert Graysmith makes this claim about the Zodiac’s 408-character cryptogram:
Fifty-five characters comprise a very complicated cipher. Was this a totally original code or had Zodiac used other sources to build his cipher system? If he had used particular books on code, perhaps these could be traced back to him.
I began by looking for basic books on secret writing. In the preface to The Codebreakers by David Kahn a sample cipher alphabet is presented; eight of the twenty-six suggested equivalents had been used by the killer. The Zodiac must have had a copy of this book.
That is a very strong conclusion. Is it true? Here’s the sample cipher from Kahn’s book:

So, if you use Kahn’s cipher alphabet on the message “CAT”, you’d get “QLK.”
Graysmith says Zodiac used eight of those equivalents. But if you look at the key to the 408-character cipher,
he really only used three of the equivalents:
(more…)
Wired Magazine reminds us of humanity’s failure to unlock the secrets of seven famous codes in their recent article, “7 Codes You’ll Never Ever Break“.
The list features some of the usual well-known mysteries, including the Zodiac Killer’s 340-character cryptogram. Which we’ll never ever break. Unless you prove them wrong. You’re working on that, right?
I’m curious to know who wrote the Concerned Citizen key, a mysterious correspondence that produces an accurate solution to the Zodiac Killer’s 3-part cryptogram. The key was sent to the police a day after the Hardens’ solution was published in the newspapers. Was it derived from the published solution? Was it an independent solve? Did it come from the killer himself? Maybe if we compare the key to the Hardens’ solution, picking through all the errors and oddities, we can gain some insight into how the Concerned Citizen key was created
I haven’t come to any conclusions, but here are the results of the analysis, which became more extensive than I originally planned:
Detailed analysis of Harden solution and Concerned Citizen key
Here’s some of the information you’ll find there:
- A detailed, annotated solution to the cipher based on the Hardens’ worksheets.

The annotations link to notes containing many observations about the various errors and other interesting information gained directly from the Hardens’ worksheets. - The Harden key, showing cipher to plain text assignments:

Plain text to cipher assignments:

And a visualization of homophone cycles:

- Detailed differences between the Hardens’ solution and the Concerned Citizen key
- FBI cryptanalysis and interpretation

The following is a summary of the findings (many of these have been discussed before; see [1] and [2]):
(more…)



Recent Comments